
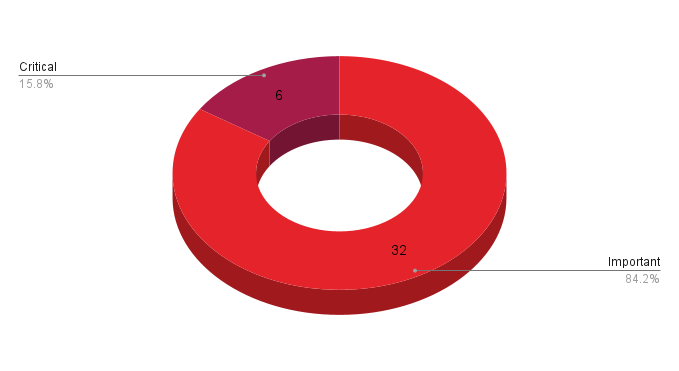
Microsoft has fixed 49 vulnerabilities in its May 2023 Patch Tuesday edition.
Below is the list of the addressed vulnerabilities in the May 2023 Patch Tuesday release:
| Tag | CVE ID | CVE Title | Severity |
|---|---|---|---|
| Microsoft Bluetooth Driver | CVE-2023-24947 | Windows Bluetooth Driver Remote Code Execution Vulnerability | Important |
| Microsoft Bluetooth Driver | CVE-2023-24948 | Windows Bluetooth Driver Elevation of Privilege Vulnerability | Important |
| Microsoft Bluetooth Driver | CVE-2023-24944 | Windows Bluetooth Driver Information Disclosure Vulnerability | Important |
| Microsoft Edge (Chromium-based) | CVE-2023-29354 | Microsoft Edge (Chromium-based) Security Feature Bypass Vulnerability | Moderate |
| Microsoft Edge (Chromium-based) | CVE-2023-2468 | Chromium: CVE-2023-2468 Inappropriate implementation in PictureInPicture | Unknown |
| Microsoft Edge (Chromium-based) | CVE-2023-2459 | Chromium: CVE-2023-2459 Inappropriate implementation in Prompts | Unknown |
| Microsoft Edge (Chromium-based) | CVE-2023-29350 | Microsoft Edge (Chromium-based) Elevation of Privilege Vulnerability | Important |
| Microsoft Edge (Chromium-based) | CVE-2023-2467 | Chromium: CVE-2023-2467 Inappropriate implementation in Prompts | Unknown |
| Microsoft Edge (Chromium-based) | CVE-2023-2463 | Chromium: CVE-2023-2463 Inappropriate implementation in Full Screen Mode | Unknown |
| Microsoft Edge (Chromium-based) | CVE-2023-2462 | Chromium: CVE-2023-2462 Inappropriate implementation in Prompts | Unknown |
| Microsoft Edge (Chromium-based) | CVE-2023-2460 | Chromium: CVE-2023-2460 Insufficient validation of untrusted input in Extensions | Unknown |
| Microsoft Edge (Chromium-based) | CVE-2023-2465 | Chromium: CVE-2023-2465 Inappropriate implementation in CORS | Unknown |
| Microsoft Edge (Chromium-based) | CVE-2023-2466 | Chromium: CVE-2023-2466 Inappropriate implementation in Prompts | Unknown |
| Microsoft Edge (Chromium-based) | CVE-2023-2464 | Chromium: CVE-2023-2464 Inappropriate implementation in PictureInPicture | Unknown |
| Microsoft Graphics Component | CVE-2023-24899 | Windows Graphics Component Elevation of Privilege Vulnerability | Important |
| Microsoft Office | CVE-2023-29344 | Microsoft Office Remote Code Execution Vulnerability | Important |
| Microsoft Office Access | CVE-2023-29333 | Microsoft Access Denial of Service Vulnerability | Important |
| Microsoft Office Excel | CVE-2023-24953 | Microsoft Excel Remote Code Execution Vulnerability | Important |
| Microsoft Office SharePoint | CVE-2023-24955 | Microsoft SharePoint Server Remote Code Execution Vulnerability | Critical |
| Microsoft Office SharePoint | CVE-2023-24954 | Microsoft SharePoint Server Information Disclosure Vulnerability | Important |
| Microsoft Office SharePoint | CVE-2023-24950 | Microsoft SharePoint Server Spoofing Vulnerability | Important |
| Microsoft Office Word | CVE-2023-29335 | Microsoft Word Security Feature Bypass Vulnerability | Important |
| Microsoft Teams | CVE-2023-24881 | Microsoft Teams Information Disclosure Vulnerability | Important |
| Microsoft Windows Codecs Library | CVE-2023-29340 | AV1 Video Extension Remote Code Execution Vulnerability | Important |
| Microsoft Windows Codecs Library | CVE-2023-29341 | AV1 Video Extension Remote Code Execution Vulnerability | Important |
| Remote Desktop Client | CVE-2023-24905 | Remote Desktop Client Remote Code Execution Vulnerability | Important |
| SysInternals | CVE-2023-29343 | SysInternals Sysmon for Windows Elevation of Privilege Vulnerability | Important |
| Visual Studio Code | CVE-2023-29338 | Visual Studio Code Information Disclosure Vulnerability | Important |
| Windows Backup Engine | CVE-2023-24946 | Windows Backup Service Elevation of Privilege Vulnerability | Important |
| Windows Installer | CVE-2023-24904 | Windows Installer Elevation of Privilege Vulnerability | Important |
| Windows iSCSI Target Service | CVE-2023-24945 | Windows iSCSI Target Service Information Disclosure Vulnerability | Important |
| Windows Kernel | CVE-2023-24949 | Windows Kernel Elevation of Privilege Vulnerability | Important |
| Windows LDAP – Lightweight Directory Access Protocol | CVE-2023-28283 | Windows Lightweight Directory Access Protocol (LDAP) Remote Code Execution Vulnerability | Critical |
| Windows MSHTML Platform | CVE-2023-29324 | Windows MSHTML Platform Security Feature Bypass Vulnerability | Important |
| Windows Network File System | CVE-2023-24941 | Windows Network File System Remote Code Execution Vulnerability | Critical |
| Windows NFS Portmapper | CVE-2023-24901 | Windows NFS Portmapper Information Disclosure Vulnerability | Important |
| Windows NFS Portmapper | CVE-2023-24939 | Server for NFS Denial of Service Vulnerability | Important |
| Windows NTLM | CVE-2023-24900 | Windows NTLM Security Support Provider Information Disclosure Vulnerability | Important |
| Windows OLE | CVE-2023-29325 | Windows OLE Remote Code Execution Vulnerability | Critical |
| Windows PGM | CVE-2023-24940 | Windows Pragmatic General Multicast (PGM) Denial of Service Vulnerability | Important |
| Windows PGM | CVE-2023-24943 | Windows Pragmatic General Multicast (PGM) Remote Code Execution Vulnerability | Critical |
| Windows RDP Client | CVE-2023-28290 | Microsoft Remote Desktop app for Windows Information Disclosure Vulnerability | Important |
| Windows Remote Procedure Call Runtime | CVE-2023-24942 | Remote Procedure Call Runtime Denial of Service Vulnerability | Important |
| Windows Secure Boot | CVE-2023-28251 | Windows Driver Revocation List Security Feature Bypass Vulnerability | Important |
| Windows Secure Boot | CVE-2023-24932 | Secure Boot Security Feature Bypass Vulnerability | Important |
| Windows Secure Socket Tunneling Protocol (SSTP) | CVE-2023-24903 | Windows Secure Socket Tunneling Protocol (SSTP) Remote Code Execution Vulnerability | Critical |
| Windows SMB | CVE-2023-24898 | Windows SMB Denial of Service Vulnerability | Important |
| Windows Win32K | CVE-2023-29336 | Win32k Elevation of Privilege Vulnerability | Important |
| Windows Win32K | CVE-2023-24902 | Win32k Elevation of Privilege Vulnerability | Important |
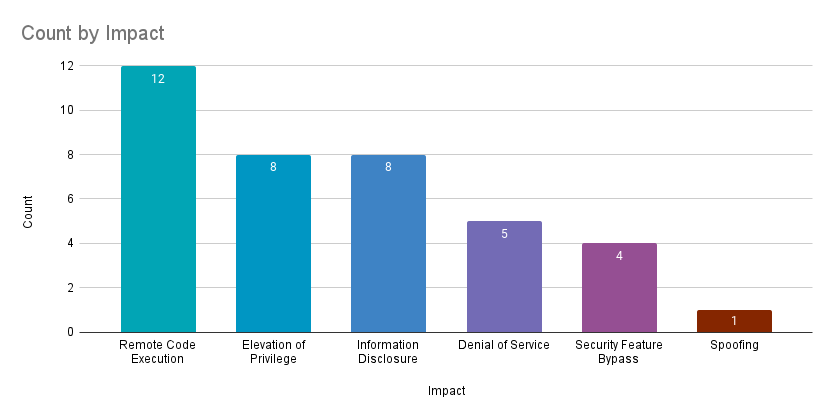
Count By Impact
Important Links and References:
https://msrc.microsoft.com/update-guide/
https://krebsonsecurity.com/2023/05/microsoft-patch-tuesday-may-2023-edition/
https://www.tenable.com/blog/microsofts-may-2023-patch-tuesday-addresses-38-cves-cve-2023-29336
About Author:

Suman Tiwari is a Cyber Security Professional by Profession and photographer by passion.
His Linkedin profile can be visited here for more details.
