The Emotet banking trojan was first identified in 2014. Emotet was originally designed as a banking malware that attempted to sneak onto your computer and steal sensitive and private information. Later versions of the software saw the addition of spamming and malware delivery services—including other banking Trojans
What is Emotet?
Emotet is a Trojan that is primarily spread through spam emails (malspam). The infection may arrive either via malicious script, macro-enabled document files, or malicious link.
Emotet may try to persuade users to click the malicious files by using tempting language about “Your Invoice,” “Payment Details,” ”Order Details” or possibly an upcoming shipment from well-known parcel companies.
Emotet is polymorphic, which means it can change itself every time it is downloaded, evading signature-based detection.
How does Emotet spread:
It can be spread through phishing spam emails containing malicious attachments or links
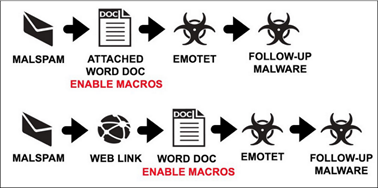
How to detect Emotet infection as Security Engineer/ SOC engineer:
Network IDS rule to catch emotet: Suricata /Snort rule:
alert http $EXTERNAL_NET any -> $HOME_NET any (msg:”ET TROJAN Possible malicious Office doc hidden in XML file”; flow:established,from_server; file_data; content:”<?xml”; within:5; content:””; nocase; distance:0; content:”macrosPresent=|22|yes|22|”; distance:0; fast_pattern; reference:url,trustwave.com/Resources/SpiderLabs-Blog/Attackers-concealing-malicious-macros-in-XML-files/; classtype:trojan-activity; sid:2020657; rev:2; metadata:created_at 2015_03_09, updated_at 2015_03_09;
Alert will is created when traffic pattern matches to above rule.
Recently, we are seeing a resurgence of Emotet with some variance in it and now being downloaded in XML format which includes Base64 encoded malicious instructions/macro
Hidden in this seemingly harmless XML file is a malicious macro document file which is compressed, encoded in base64, and stored in XML format. Below is diagram showing how the malicious document was stored.

Investigation:
Download the file from the host and scan in through virustotal or metadefender.
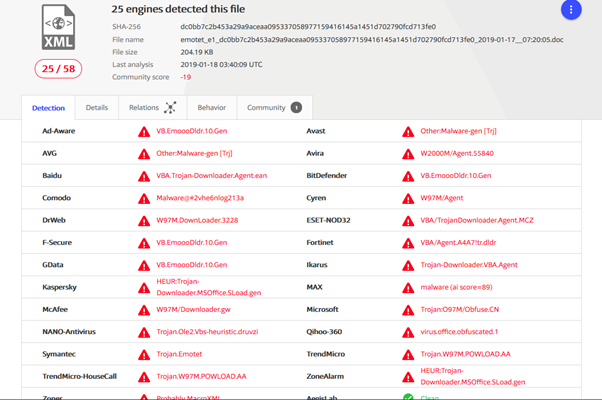
After analysing on VT, we can use sandbox to analyse the exact behaviour of the file.
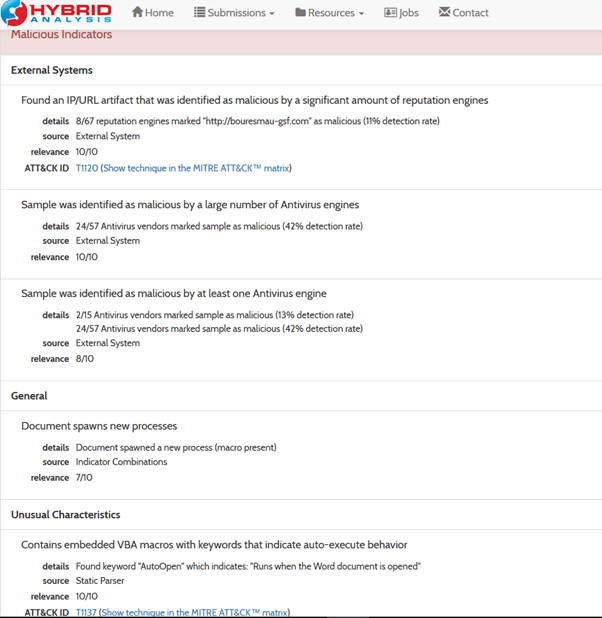
We can use hybrid analysis tool to see the mal doc behavior:
Above link contains well detailed analysis of the emotet file. Below are some screenshots of analysis:
Apart from this we can use can install “Oletools” for quick manual analysis: (Also, for analysts willing to play around the code)
Below are few snapshots of method and result of manual analysis of a malicious document:
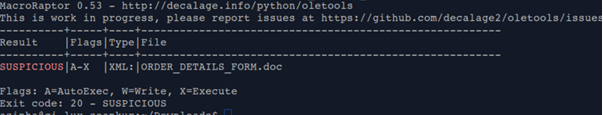
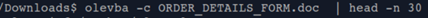
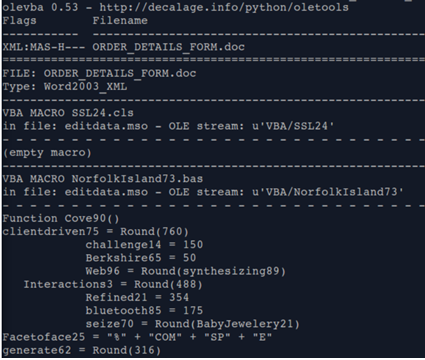
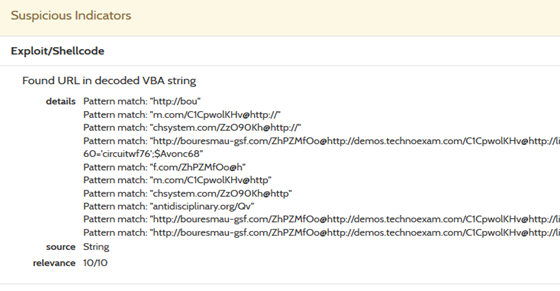
Using this tool or hybrid analysis we can extract Trojan Downloaders- in this case (5 potential payload domains) as below:
hxxp:/ /koor[dot]com/PbEu786
www[dot]antique-carpets[dot]com/PIpK4IlRd
hxxp:/ /buyhomecare[dot]ne/RyoJj06
hxxp://amallrca[dot]org/Jw3mayRvk
hxxp:/ /kangtc[dot]com/WRCk6xGo9s
Once we are sure of infection the only way to stop is to isolate the host and then reimage the host back.
For NON IT professional Guys:
If you receive any email with some attachment from unknown sources always make sure do not open it straight away, because opening it enable macros leading to emotet infection which can spread out in entire organization.
You’re already taking the first step towards protecting yourself and your users from Emotet by reading this. Here’s a few additional steps you can take:
- Keep your computer/endpoints up-to-date with the latest patches for Microsoft Windows. Emotet may rely on the Windows EternalBlue vulnerability to do its dirty work, so don’t leave that back door open into your network.
- Don’t download suspicious attachments or click a shady-looking link. Emotet can’t get that initial foothold on your system or network if you avoid those suspect emails. Take the time to educate your users on how to spot malspam.
Sign of emotet infected device:
Payload downloaded is usually dropped in Users\Public\ directory and named as random numbers between 1 – 5 digits long (the filename can be found in the Powershell command issued to download the files)
Payload moves a copy of itself in to a newly created folder in appdata\local
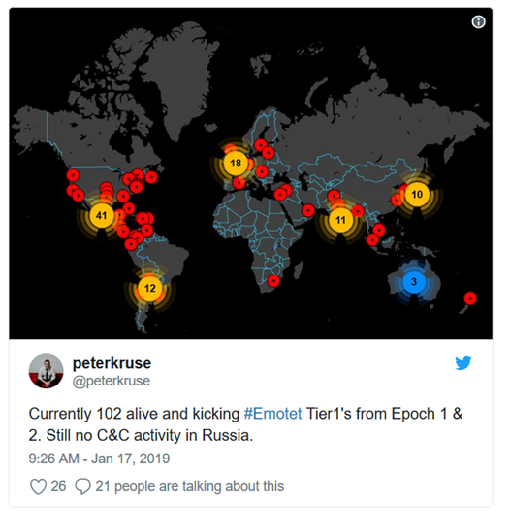
Current Emotet outbreak level in world:
Author : Rajat Bajpai

Rajat Bajpai has done Master in Engineering in Information and Network Security from University of Limerick. He is having approx 2 years of experience and currently working with eSentire Inc., Cork as a SOC Analyst.
His job as a security Analyst involves him in dealing with day to day cyber attacks and exploits.
Attacks and exploits keep on changing and attackers keep modifying their attack patterns and attack vectors. In-order to deal with such attacks, Rajat keep updating himself and act as first line of defense against all such attacks.

2COMMENTS
Nice article Rajat.
Nice initiative by Phototor.com.
Keep up the good work.
Also, go through this link. It’s very informative especially the countermeasures and best practices part.
https://www.cyberswachhtakendra.gov.in/alerts/emotet.html
Thnku Andrew